C
With Cyber Gate EDR, security experts detect suspicious activity from all network-connected devices and quickly eliminate threats.
Endpoint security
Ensures the protection of all devices connected to the corporate network.
Threat detection
Identify threats using behavioral analysis.
Incident management
It allows you to focus on threats in order of priority.
Flexible response
Block attacks and contain threats in real time.
Before understanding what the EDR solution is, let’s start with the definition of Endpoint.
An endpoint is any device capable of connecting to the corporate network.
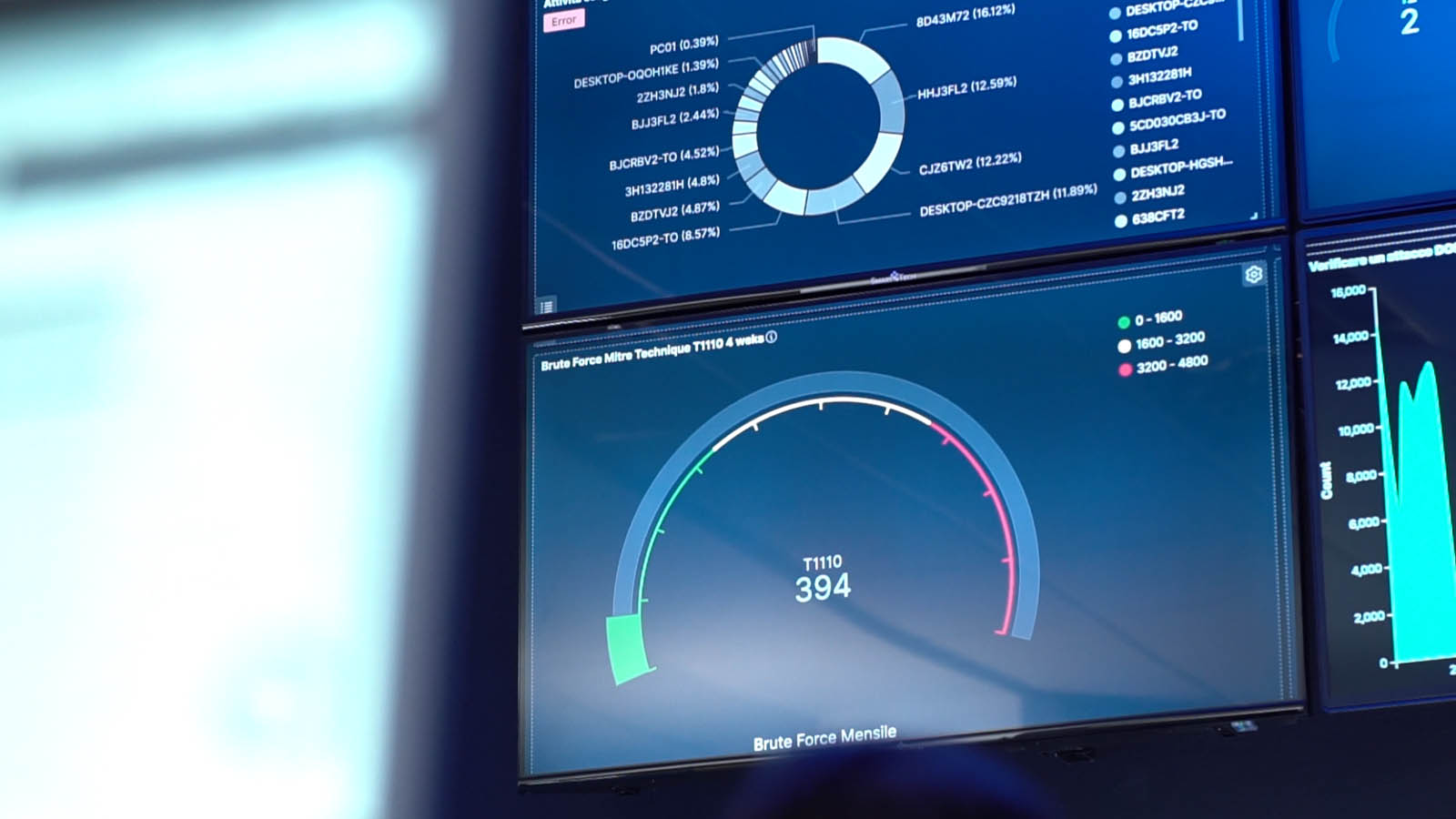
With EDR technology – Endpoint Detection and Response – it is possible to analyze in real time what happens on each endpoint and allows to detect anomalies through the integrated analysis of all devices.
By analyzing data and behavioral analysis with artificial intelligence algorithms, we can detect threats that are not visible by traditional protection systems. finally, EDR offers the possibility of responding immediately to the threats detected.
The Cyber Gate integrates the potential of EDR solutions with those of threat intelligence, machine learning and artificial intelligence.
The use of these systems involves complete protection not only on malware but on any anomalous activity found on your devices.
It performs a series of automated scans and checks in order to detect the presence of existing threats and block them.
Record all the information that comes from the behavioral analysis.
It analyzes threats and ranks them in order of priority.
It undertakes necessary countermeasures to block cyber threats.
After identifying new threats, strengthen the prevention plan to increase the level of security.
Stops malware and ransomware
Prevents the launch of malicious executable files with various prevention methods. It reduces attacks and increases the accuracy of malware prevention.
Provides behavior-based protection
Detect and stop attacks by monitoring malicious behavior through a sequence of events.
Blocks exploits and fileless attacks
Blocks exploit techniques used by attacks by disrupting the attack life cycle and rendering threats ineffective.
Coordinates the application with the network and the cloud
Tight integration between network, endpoint and cloud enables continuous security improvement and provides multi-layered prevention from 0-day attacks.
The goal is to solve the limits of antivirus, allowing you to have a picture
complete and detailed visibility of the clients present in the company.
Having an external team of professionals who monitor your computer network 24/7 is a fundamental step to increase the level of protection and immediate response to cyber threats.
The service includes:

The team is made up of experienced security analysts, system engineers and malware specialists. They work to detect threats and respond to attacks 24/7.






T. +39 030 5357 143
E. info@savyng.it
VAT 04170250981
Savyng Srls
Via Lazzaretto, 2
25030 Adro (BS) Italy
Do you need Cyber Security and Privacy services to guarantee the right IT security in the company?